Artificial Intelligence
Software & DevOps
No posts found
Cloud Computing
No posts found
Blockchain
Recent Posts
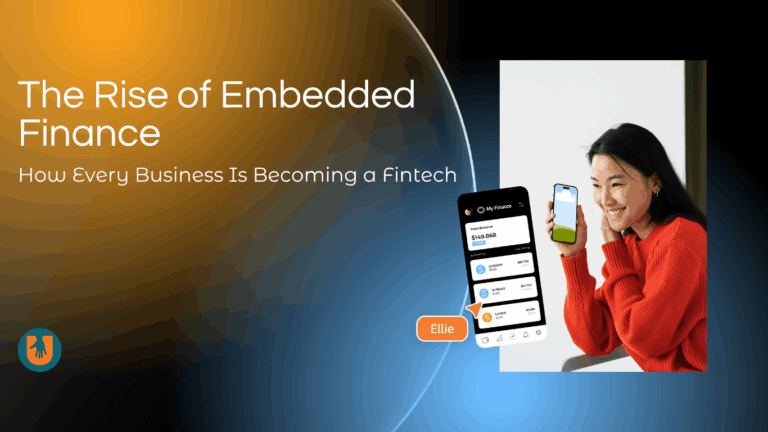
What is Embedded Finance? Defining the Invisible Revolution 💰 The Core Models: How Businesses Are Embedding Finance 🏪 The Core Technologies Powering Embedded Finance 📲 Key...
QR code phishing, also called quishing, is a fast-growing cyber threat. Attackers hide scams inside QR codes placed on posters, menus, or emails. When scanned, these codes...
Why This Matters Now What’s Ahead How Surveillance Changed Why Governments Use Surveillance What Privacy Advocates Fear When Surveillance Goes Wrong West vs. Authoritarian...
What Are AI Powered Startups? 🌻 Why Founders Are Turning to AI ↗️ Industries Being Disrupted by AI Startups 🏭 ▪️Healthcare ▪️Finance ▪️Retail & E-commerce ▪️Agriculture...
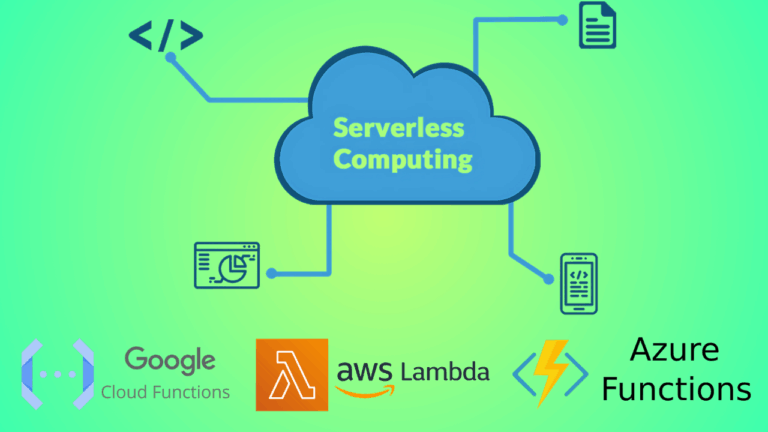
Introduction 🌤️ What is Serverless Computing? ⌨️ Key Characteristics Event-driven architecture Auto-scaling Pay-as-you-go pricing model How Serverless Computing Works 🛠️ Function-as-a-Service...
Introduction What Is AI and Blockchain Integration? How Does It Work? Real-World Examples Key Benefits of AI and Blockchain Working Together Enhanced Data Security and Transparency...
You know how you type a website name into your browser, and it just works? That’s DNS—Domain Name System. It’s basically the internet’s phone book, turning names like google.com...
Introduction 🌿 Why PETs Are Important What Are Privacy-Enhancing Technologies (PETs)? 🪪 Common Features of PETs Types of PETs 🔏 Encryption Anonymization Techniques Differential...
No posts found