Table of Contents
In the context of cybersecurity, a security protocol is a collection of rules or processes that control data transfer and exchange between two or more devices over a network. These protocols are intended to secure the integrity, confidentiality, and authenticity of the data being communicated, hence preventing unauthorised access, alteration, or destruction.
Security procedures are extremely important in the field of cybersecurity. They are the foundation of secure communication, allowing sensitive information to be safely transmitted across potentially insecure networks like the internet. Without these standards, the data we transmit and receive online, including personal communications and financial transactions, would be subject to a wide range of cyber dangers.
The History and Evolution of SSL/TLS ⌛
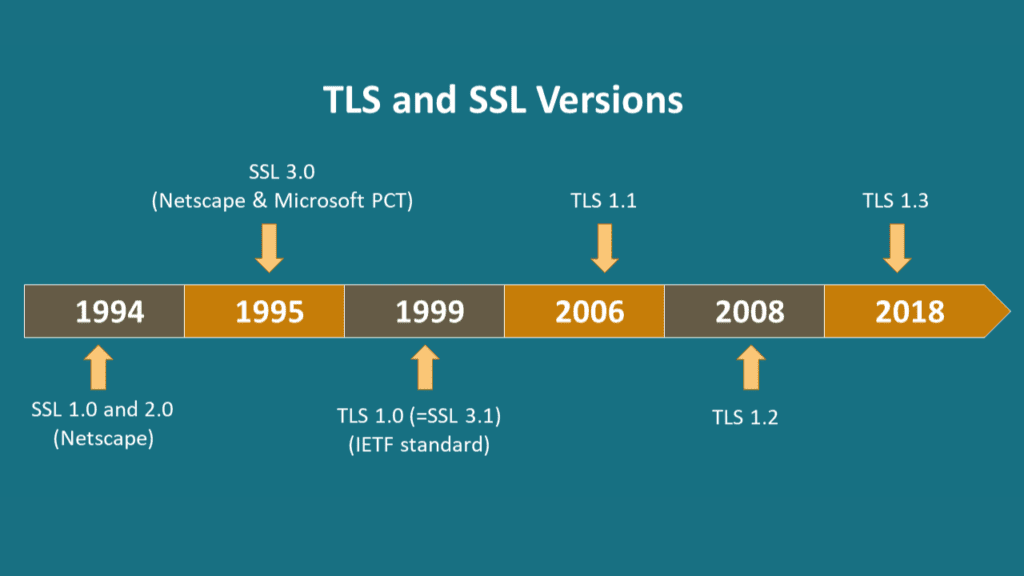
Netscape originally released the Secure Sockets Layer (SSL) version 1.0 technology in 1994. The Internet was expanding, and there was a demand for transport security for web browsers and numerous TCP protocols. Version 1.0 of SSL was never published due to major security issues. SSL’s first official release, version 2.0, was out in 1995. It was made by using the MD-52 algorithm.
This early version of SSL enabled basic encryption, but it had numerous security issues, including the use of insecure cryptographic techniques and a lack of adequate authorization. These limitations were right away addressed, resulting in the creation of SSL 3.0.
The final version of the SSL protocol, SSL 3.0, was released in November 1996.SSL 3.0 addressed many of the security vulnerabilities present in SSL 2.0, adding stronger encryption algorithms and better authentication mechanisms. It became widely adopted and served as the foundation for the later TLS protocol.
The IETF (Internet Engineering Task Force) released the Transport Layer Security (TLS) protocol version 1.0 in 1999 as an upgrade to SSL v3. According to the TLS 1.0 RFC document (RFC 2246), the variations between TLS 1.0 and SSL 3.0 are not dramatic but rather notable enough to forbid compatibility.
The Internet Engineering Task Force (IETF) declared in 2011 that SSL version 2.0 is no longer supported. The IETF advised that SSL v2 be fully abandoned since, according to a paper they published (RFC 6176), the protocol has numerous fundamental flaws. These included utilising MD5 for message authentication, without protecting handshakes, using the same key for message integrity and encryption, and allowing for simple session termination.
TLS 1.1 (RFC 4346) was a minor update to TLS 1.0 released in April 2006. Some of the differences in this version included protections against Cipher Block Chaining (CBC) attacks.
TLS 1.2 (RFC 5246) was released in August 2008. Changes included adding cipher-suite-specified pseudorandom functions (PRFs), adding AES cipher suites, removing IDEA and DES cipher suites, and several other enhancements.
In June 2015, IETF also announced that SSL 3.0 is deprecated. As stated in a document released by IETF (RFC 7568), any TLS version is more secure than all versions of SSL. SSL also cannot use features of the TLS protocol such as Authenticated Encryption with Additional Data (AEAD), Elliptic Curve Diffie-Hellman (ECDH) and Elliptic Curve Digital Signature Algorithm (ECDSA), stateless session tickets, a datagram mode of operation (DTLS) and application-layer protocol negotiation.
The current version of TLS, TLS 1.3, was released in August 2018 (RFC 8446). It took IETF 10 years and 28 drafts to complete. This time, the protocol underwent some major changes with the focus on simplicity. Several unsafe technologies were removed, including SHA-1, MD5, RC4, DES, and 3DES. The protocol was streamlined for better performance: the handshake now requires only one round-trip (in some cases even zero). Other changes include encryption of SNI information for better privacy and a new signature standard (RSA-PSS). All modern browsers support TLS v1.3.
Some of the most significant milestones 🚀
📌 2006: Microsoft announces it will offer SSL protection across its entire product portfolio
Back in 2006, Microsoft made a big move to step up its security game by announcing that it would roll out SSL protection across its entire product lineup, including Windows Mobile devices. This was part of their push to make sure everything from Windows operating systems to Office tools and even mobile devices could securely handle sensitive data.
At a time when cyber threats were growing, this was a major step forward, especially for mobile users who were starting to rely more on their devices for emails and web browsing. By integrating SSL/TLS encryption, Microsoft not only aimed to protect users from hackers but also to set a higher standard for secure communication across the tech industry. It was a clear signal that security was no longer optional—it was essential.
📌 2010: Introduction of SSL/TLS for All Websites
A significant push for universal SSL adoption began in the 2010s, especially as search engines and browsers started prioritizing HTTPS. Google said in 2014 that it will prioritise search results using HTTPS, therefore motivating websites to obtain SSL/TLS certificates. Chrome and Firefox started labelling HTTP sites as “Not Secure,” therefore hastening SSL acceptance by 2018. This change made HTTPS the norm for safe browsing—even on non-commerce sites.
📌 2016: Let’s Encrypt Launch
In 2016, Let’s Encrypt made a huge splash in the world of web security by offering free SSL/TLS certificates to anyone who wanted them. Before that, getting a certificate could be costly and complicated, especially for smaller websites or hobbyists. But Let’s Encrypt changed all that. They made it possible for anyone—whether you’re running a small blog or a big business—to get a secure connection for their website without paying a dime. The best part? They automated the process, making it easy for website owners to get and renew certificates without the usual hassle. This move helped push the entire web towards HTTPS, improving overall security and privacy online. It was a game-changer, and it’s one of the key reasons we’ve seen such widespread adoption of SSL/TLS in recent years.
📌 2020: The Push for HTTPS Everywhere
HTTPS Everywhere has being heavily pushed in the 2020s, implying that SSL/TLS encryption should be used on all websites—not just those processing credit card or personal data. Growing consciousness of the value of internet privacy and security motivated this change. Leading participants in this initiative have been major companies like Google and Mozilla; Google even notes HTTP sites as “Not Secure” in Chrome. Whether you’re reading a news item, shopping online, or checking your email, encryption ought to be the default for every website.
HTTPS guarantees users that their data is secured and guarded from prying eyes, therefore rendering the web safer for everybody. Better search results for HTTPS-enabled websites also follow from this change, which motivates even more website owners to migrate. Privacy and security gain from this; it’s all about ensuring that your data remains safe wherever you are surfing.
Google has continued to push for stronger security by deprecating older, insecure versions of TLS (e.g., TLS 1.0 and 1.1) and encouraging the adoption of TLS 1.2 and TLS 1.3.
How SSL/TLS Protocols Work 🛠️
🤝 Handshake Process
The handshake procedure starts the first thing you notice when visiting an SSL/TLS-using website. Consider it as a secret handshake between your browser and the website ensuring their security of communication. Here’s how it goes:
- Hello from the Browser Your browser asks whether it may use SSL/TLS for a safe connection and says “Hi” to the website.
- The website responds with, “Sure, I’m ready to encrypt the data.” It also provides a specific certificate attesting to its authenticity as the official website rather than a phoney.
- Your browser and the website then agree on a secret code—called an encryption key—that only you will know. The data is scrambled using this code such that none else may access it.
- At last, both parties certify that everything is in place for a safe and secure connection. Once they are both content, the “handshake” is completed, and now they may begin data sharing knowing it is encrypted.
Usually without your even awareness, this entire process occurs rather quickly. Nevertheless, this is the reason your data remains protected when you visit safe websites!
🔐 Encryption and Decryption
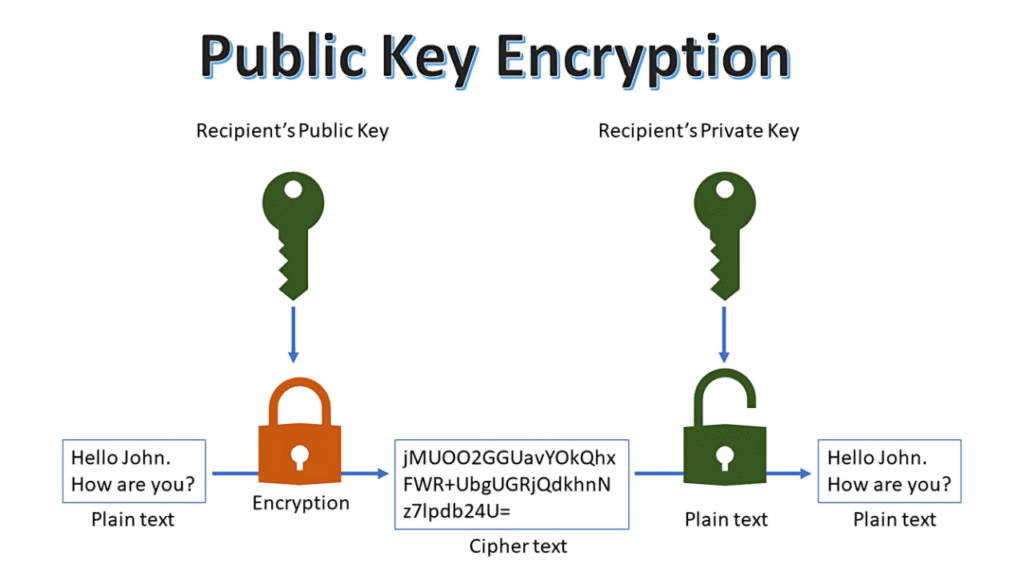
When we talk about encryption and decryption, it’s all about scrambling data so that only the intended recipient can read it. This is where public and private keys come into play—they’re the backbone of how SSL/TLS and other encryption systems work.
Here’s the process in action:
- Encryption: If someone wants to send you a secure message, they use your public key to encrypt the data. Once it’s encrypted, even they can’t read it anymore—it’s like locking the box and throwing away the key (except the public key).
- Decryption: When you receive the encrypted data, you use your private key to decrypt it. Since only you have the private key, only you can unlock and read the original message.
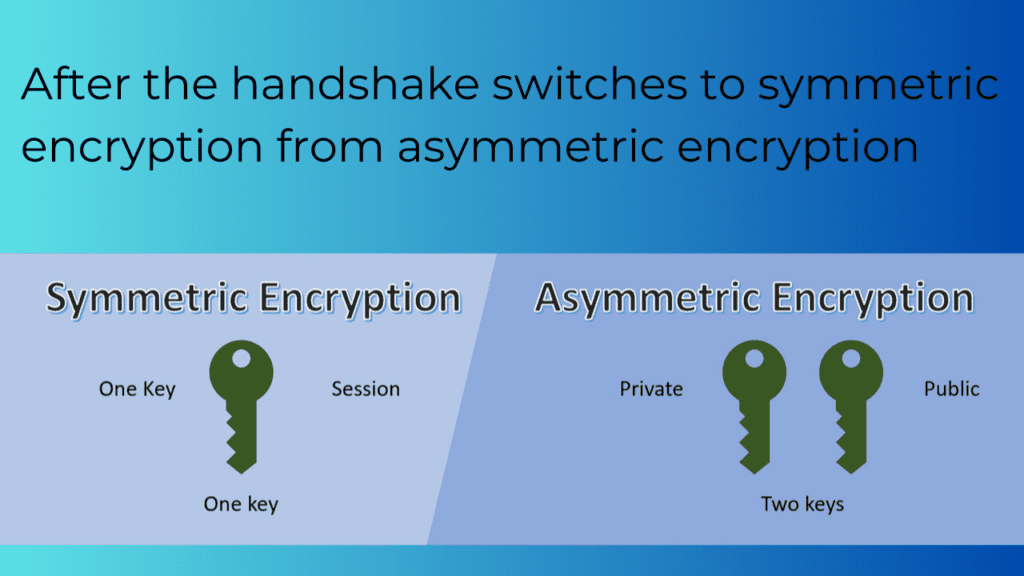
This whole system is called asymmetric encryption, and it’s what makes secure communication over the internet possible. It ensures that even if someone intercepts the encrypted data, they can’t do anything with it without the private key. Pretty neat, right?
By the way, SSL/TLS uses this mechanism during the handshake process to securely exchange keys and establish a secure connection. After that, it often switches to symmetric encryption (using a single shared key) for faster data transfer.
🗝️ Authentication
Let’s look at the technical aspects of authentication and how Certificate Authorities (CAs) play an important part in determining the validity of websites or servers. Assume you’re attempting to access a website and see the little padlock icon in the URL bar. That padlock indicates that the site is utilising SSL/TLS to encrypt your connection, but how do you know you’re talking to the legitimate website and not an imposter? This is where CAs come in.
When a website wishes to verify its identity, it obtains an SSL/TLS certificate from a reputable Certificate Authority. These CAs act as the internet’s equivalent of a notary public, ensuring that the website or server is who it claims to be. Here’s how it works: the website owner produces a public and private key, then sends the public key to the CA along with some identifying information (such as their domain name).
The CA performs its research by verifying domain ownership and, in certain cases, the legal identification of the organisation behind the website. When everything checks out, the CA provides a digital certificate, which is simply a signed declaration that states, “Yes, this public key belongs to this website.”
When your browser connects to the website, the server provides you this certificate. Your browser then compares the certificate to a list of trustworthy CAs that it already knows. If the certificate is legitimate and signed by a trusted CA, your browser utilises the certificate’s public key to create a secure connection. If something is wrong—for example, the certificate is expired, self-signed, or issued by an untrusted CA—your browser will display a warning, indicating that something fishy is going on.
In a nutshell, CAs serve as the internet’s trust infrastructure. They ensure that when you believe you’re chatting to your bank’s website, you truly are—not some smart hacker’s replica. Without them, SSL/TLS encryption would be meaningless since there would be no way to determine who is on the other end of the connection.
🔍 Integrity Checks
When we talk about SSL/TLS integrity checks, we are essentially ensuring that the data you send or receive has not been tampered with along the route. Imagine sending a sealed letter in the mail; you’d want to know whether it was opened, modified, and resealed, right? SSL/TLS works similarly, except for digital data.
This is how it works. SSL/TLS makes use of a Message Authentication Code (MAC), which is commonly done using HMAC (Hash-based Message Authentication Code).
When data is transferred, it is joined with a secret key and sent through a cryptographic hash function, resulting in a unique “fingerprint” of the data. This fingerprint is transmitted alongside the encrypted data.
On the receiving end, the procedure is repeated with the shared secret key. If the fingerprints match, it suggests the data was not tampered with. If they don’t match, it’s a red warning that something is wrong—perhaps someone tried to change the data in mid-transmission.
This entire process is included within the SSL/TLS handshake and occurs effortlessly in the background. So, whether you’re entering into your bank account or sending an email, SSL/TLS works silently to ensure that everything you transmit arrives intact and untampered.
The Impact of SSL/TLS on Cybersecurity 🎯
🛡️ Data Protection
So, you know how when you’re shopping online or logging into your bank account, you’re sending super sensitive stuff like passwords, credit card numbers, or personal info over the internet? Well, without SSL/TLS, that data would basically be sent in plain text, like a postcard anyone could read if they intercepted it. Not great, right? That’s where SSL/TLS comes in—it’s like a super-secure envelope for your data.
Here’s how it works: When your browser connects to a website using SSL/TLS, they perform this thing called a handshake. During this handshake, they agree on a secret code (encryption keys) that only they know. Once that’s set up, all the data you send and receive gets scrambled into unreadable gibberish using super strong encryption algorithms, like AES (Advanced Encryption Standard). Even if a hacker manages to intercept the data, all they’ll see is a bunch of random characters—no credit card numbers, no passwords, nada.
But it doesn’t stop there. SSL/TLS also makes sure the data hasn’t been tampered with during transit. It uses something called message integrity checks (like HMAC) to ensure that what you sent is exactly what arrives on the other end. And to top it off, SSL/TLS verifies that you’re actually talking to the real website and not some fake one set up by attackers. It does this through digital certificates, which are like ID cards issued by trusted Certificate Authorities (CAs).
So, in a nutshell, SSL/TLS is like a triple-layered shield: it encrypts your data, checks for tampering, and confirms you’re talking to the right server. That’s why it’s the gold standard for keeping your sensitive info safe online!
🛡️ Preventing Man-in-the-Middle Attacks
As we discussed above SSL/TLS acts as the ultimate bodyguard for your online communication, stopping stealthy man-in-the-middle (MITM) assaults dead in their tracks. Here’s how it works: when you connect to a website, SSL/TLS initiates a secure handshake in which your browser and server exchange cryptographic keys to form an encrypted tunnel.
This implies that if an attacker attempts to eavesdrop on your data, they will only see jumbled nonsense. Furthermore, SSL/TLS employs digital certificates to validate the server’s authenticity, so you know you’re dealing with the actual thing and not some impostor attempting to mess with your information. In brief, SSL/TLS ensures that your data remains safe, undamaged, and out of the hands of hackers.
🛡️ Trust and Authentication
SSL/TLS certificates play an important role in establishing user confidence by assuring that websites are genuine and safe. When a website utilises SSL/TLS, it displays a digital certificate issued by a reputable Certificate Authority (CA) that authenticates the site’s identity. This method not only encrypts data but also validates to users that they are engaging with a real site rather than a fraudulent one created by attackers.
For example, the padlock icon or “https://” in your browser indicates that the site has been validated and your connection is safe. This helps to avoid phishing attempts, in which hackers attempt to fool users into inputting important information on bogus websites. SSL/TLS provides a safer online experience by integrating encryption and identity verification, increasing confidence in both consumers and companies.
🛡️ Impact on Online Privacy
The growing importance of encryption for online privacy has become impossible to ignore, especially with the surge in data breaches over the past decade. SSL/TLS protocols, like the ones Microsoft rolled out across its product portfolio back in 2006, have played a critical role in safeguarding sensitive data—whether it’s passwords, credit card info, or personal messages. As cyberattacks grew more sophisticated, encryption became the first line of defense, ensuring that even if data was intercepted, it would remain unreadable to hackers.
With high-profile breaches exposing millions of users’ data, the push for universal HTTPS adoption, led by companies like Google, has made encryption a non-negotiable standard. Today, SSL/TLS isn’t just about security; it’s about building trust and ensuring privacy in an increasingly connected world.
The Future of SSL/TLS and Web Security 🌱
The future of SSL/TLS and web security is looking brighter as there’s a global push for stronger encryption. More and more websites are adopting HTTPS to ensure data is protected, and major browsers like Chrome and Firefox are making it a requirement. They’ve even started marking HTTP sites as “Not Secure,” urging website owners to upgrade their security. This is all part of the effort to make sure every site on the internet keeps your data safe while you browse.
But even as SSL/TLS becomes the standard, there are still some challenges ahead. One big issue is the growing computational power of cyber attackers. As technology improves, hackers have more tools at their disposal to crack encryption. This means that SSL/TLS protocols need to keep evolving to stay one step ahead. Stronger encryption and better cryptographic practices will be needed to keep up with these growing threats.
Looking further into the future, we’re entering an era of post-quantum cryptography. Quantum computers, which are still in development, could eventually have the power to break current encryption methods. To prepare for that, researchers are working on new cryptographic algorithms that will be resistant to quantum attacks. SSL/TLS protocols will need to adopt these quantum-safe algorithms to secure data in a world where traditional encryption could be at risk. So, while the future presents some challenges, it also promises exciting new advancements in web security.
FAQ 💡
What is an SSL/TLS certificate, and why is it necessary?
An SSL/TLS certificate is a digital document that verifies a website’s identity and enables encrypted communication. It contains the website’s public key, domain name, and the issuing Certificate Authority (CA). Without a valid certificate, browsers cannot establish a secure HTTPS connection, leaving data vulnerable to interception.
Why is SSL/TLS important for cybersecurity?
SSL/TLS protocols are essential for protecting sensitive information, like passwords, credit card numbers, and personal data, during online transactions. They encrypt data, ensuring that it cannot be intercepted or altered by hackers. SSL/TLS also provides authentication, confirming that the website you’re communicating with is legitimate, preventing cyberattacks such as man-in-the-middle attacks and phishing.
What is the difference between SSL and TLS?
SSL (Secure Sockets Layer) and TLS (Transport Layer Security) are both cryptographic protocols designed to secure online communications. SSL is the older protocol, which has been largely replaced by TLS due to its stronger security features. TLS is more secure and efficient, offering better encryption and protection against vulnerabilities that SSL had. While people still refer to SSL, most modern websites use TLS for secure communication.
How do I know if a website is using SSL/TLS?
You can tell if a website uses SSL/TLS by checking the browser’s address bar. A padlock icon and “https://” (instead of “http://”) indicate that the connection is secure. Modern browsers also flag websites without SSL/TLS as “Not Secure.”
What are the risks of not using SSL/TLS on a website?
Without SSL/TLS, data transmitted between the user and the website is sent in plaintext, making it easy for hackers to intercept and steal sensitive information. Additionally, websites without HTTPS are flagged as insecure by browsers, which can deter visitors and harm credibility. Non-compliance with regulations like GDPR or PCI DSS can also lead to legal and financial penalties.
Can SSL/TLS be hacked, and how can I protect against vulnerabilities?
While SSL/TLS is highly secure, vulnerabilities like Heartbleed, POODLE, and BEAST have been discovered in older versions. To protect against these, always use the latest version of TLS (e.g., TLS 1.3), keep software and certificates up to date, and disable outdated protocols like SSL 2.0/3.0 and TLS 1.0/1.1.
Can SSL/TLS certificates expire?
Yes, SSL/TLS certificates have an expiration date. Typically, they last for one or two years before they need to be renewed. If a website’s certificate expires, the encrypted connection may no longer be valid, and users may see warnings in their browser. Regular renewal is essential to ensure continuous security.
Why are SSL/TLS certificates important for SEO?
Google and other search engines favor websites that use HTTPS (secured by SSL/TLS certificates). Having an SSL/TLS certificate can improve your website’s ranking in search engine results, as HTTPS is considered a ranking factor. It also enhances user trust, as visitors feel more confident browsing secure sites.
What is a Certificate Authority (CA), and why is it important?
A Certificate Authority (CA) is a trusted organization that issues SSL/TLS certificates. CAs verify the identity of the certificate requester (e.g., a website owner) and ensure the certificate is valid. Browsers and operating systems trust certificates issued by recognized CAs, which is why they are essential for establishing secure connections.
What are the most common SSL/TLS vulnerabilities, and how can they be mitigated?
Common vulnerabilities include:
Heartbleed: A bug in OpenSSL that leaks sensitive data. Mitigation: Update OpenSSL to the latest version.
POODLE: Exploits SSL 3.0 to decrypt data. Mitigation: Disable SSL 3.0 and use TLS 1.2 or higher.
BEAST: Targets TLS 1.0 to decrypt encrypted data. Mitigation: Upgrade to TLS 1.2 or 1.3.
Regular updates, disabling outdated protocols, and using strong encryption algorithms can mitigate these risks.
How does SSL/TLS impact mobile app security?
SSL/TLS is critical for securing data transmitted by mobile apps, especially for sensitive operations like login, payments, and API communications. Mobile apps must implement SSL/TLS to encrypt data in transit, use certificate pinning to prevent man-in-the-middle attacks, and ensure they support the latest TLS versions for robust security.
References
- https://datatracker.ietf.org/doc/html/rfc8446
- https://transparencyreport.google.com/https/overview
- https://owasp.org/www-community/controls/Transport_Layer_Protection
- https://csrc.nist.gov/publications/detail/sp/800-52/rev-2/final
- https://letsencrypt.org/
- https://transparencyreport.google.com/https/overview