Table of Contents
QR codes are everywhere. You see them on menus, posters, ads, and even bills. A quick scan takes you to a website, app, or payment page. It feels fast and easy. That’s the point.
But this speed comes with risk. Criminals have found ways to use QR codes for phishing attacks. This type of scam has a name: quishing. It mixes “QR” and “phishing.” The trick is simple. A fake code looks like a real one. When you scan it, you may land on a fake site. From there, attackers can steal your login details, bank info, or even install malware on your device.
Quishing is not new, but it’s growing fast. People trust QR codes because they look harmless. A square pattern on a sticker doesn’t seem dangerous. That false sense of safety makes it easier for attackers to strike.
Think about how QR codes are used. You pay for food, get a bus ticket, or sign into a Wi-Fi network. In each case, you rely on the code to guide you. If the code is fake, you could be giving your private data away without knowing it.
This attack is especially sneaky. It bypasses email security. Your computer’s defenses cannot check the QR code. Your phone’s camera just opens the link. The danger is hidden until it is too late.
Businesses are also at risk. A single compromised code placed on a poster, flyer, or even inside an office can open the door to fraud. Attackers use both physical and digital tricks to spread these codes. That makes quishing a hybrid threat—blending offline tricks with online crime.
This article will explain how quishing works, why it matters, and what you can do about it. We’ll look at real cases, common risks, and smart steps to stay safe. By the end, you’ll know how to spot a scam and protect yourself from this growing danger.
What is QR Code Phishing (Quishing)? ⁉️
A QR code is a square barcode. Your phone’s camera can read it. It quickly takes you to a website. This is helpful for menus or payments. Scammers have found a way to abuse this tool.
They create a malicious QR code. This code contains a dangerous web link. The link is hidden inside the image. You cannot see it just by looking. When you scan the code, your phone opens the link. It directs you to a fraudulent website.
This fake site looks like a real one. It may mimic your email login, bank, or social media. The page will ask for your username and password. If you type them in, you give your details directly to the scammer.
The scam does not stop at login pages. Some codes may trigger a file download. This file could contain harmful software. This malware can infect your phone. It can steal other data or spy on you.
Quishing is a type of social engineering. This means it tricks people instead of hacking systems. It uses our trust in QR codes against us. We are used to scanning them for convenience. Scammers exploit this habit.
Quishing is different from standard phishing. In email phishing, you click a suspicious link. In SMS phishing, you tap a text message link. With quishing, the harmful link is tucked inside a QR code. That extra step makes it harder for people to spot danger. Most users cannot read the code itself, so they trust it without question.
Attackers also take advantage of how and where QR codes are used. You see them in both digital and physical spaces. A scammer may stick a fake code over a real one on a poster. They may add it to a flyer, parking meter, or public notice. Online, attackers may send you an email with a QR code to “verify your account” or “track a delivery.” In both cases, the code looks normal, but the goal is the same—steal your data or money.
Anyone with a phone can be a target. It happens to individuals at home. It also happens to employees at work. A single scan can compromise personal accounts. It can also breach an entire company’s network.
In short, quishing is phishing through QR codes. It blends the physical world with digital crime. Knowing what quishing is and how it works is the first step toward staying safe.The next sections will show you how these attacks work in real life.
How Does a Quishing Attack Work? The Anatomy of a Scam ⚠️
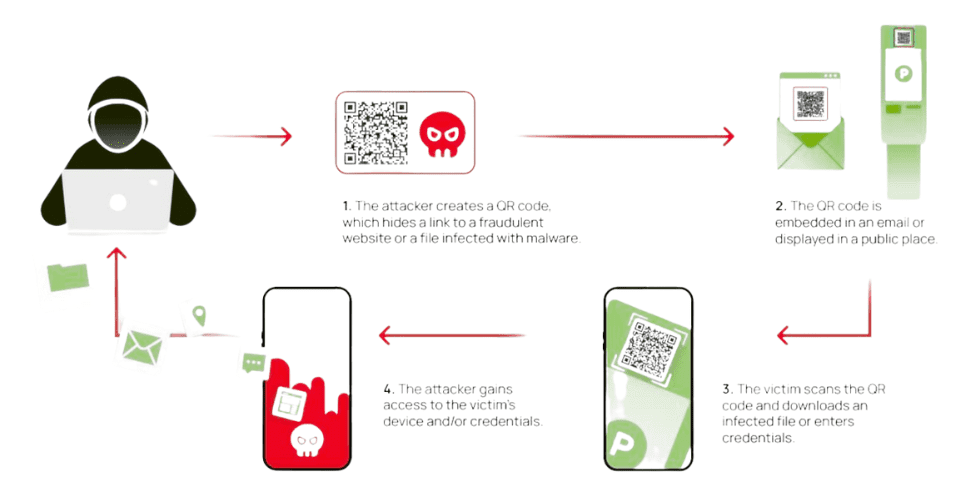
Quishing attacks may look simple, but the methods behind them are smart and targeted. Attackers know that people trust QR codes, so they use that trust to hide their tricks. Most scams follow a few common patterns.
Malicious redirects
When you scan a QR code, your phone’s camera or app reads the link inside. A normal code takes you to the correct site or app. A quishing code, however, redirects you to a fake site. These fake sites are designed to look real. They may copy a bank login page, a shopping site, or a social media account. Once you enter your details, attackers capture them instantly.
Fake websites and forms
Some codes lead to pages that ask for “verification.” They may prompt you to confirm your email, reset your password, or fill in payment info. The page looks official, but it’s only collecting your data. These forms are one of the most common tools in quishing attacks.
Credential theft and payments
Quishing is often used to steal login credentials. But it can also target direct payments. A fake code can link to a false payment gateway. In some cases, codes link to peer-to-peer payment apps, sending money directly to the attacker.
Physical manipulation
In public spaces, attackers may cover a real QR code with a fake one. You may see this on posters, ads, parking meters, or restaurant menus. Since people rarely check the source, these fake stickers go unnoticed.
Digital manipulation
Quishing also happens online. Attackers send emails with QR codes instead of links. This bypasses some email filters that block suspicious URLs. The email may claim to be from your bank, a courier, or even your workplace. Once scanned, the code leads to the same traps as physical ones—fake logins or malware downloads.
Social engineering
Attackers often mix quishing with social engineering. They use urgent language like “your account will be locked” or “your delivery is delayed.” This sense of pressure makes users act fast without thinking.
Why it works
QR codes are effective because people cannot see the link until after scanning. Unlike a normal email link, which you can hover over, the code hides the destination. That hidden nature, combined with everyday use, makes quishing harder to detect.
In short, quishing works by hiding dangerous links inside something people already trust. Whether through a sticker on a wall or an email in your inbox, the attack follows the same pattern—trick, redirect, and steal.
This is the anatomy of a quishing scam. It is a simple but effective trap. The next section will explain why this trick is so successful today.
Real-World Examples of QR Code Phishing 📧
Quishing is not just a theory. It has already caused problems for both individuals and businesses. In many cities, fake QR codes have been found on parking meters. Drivers scan what they think is the official code, only to be sent to a fake payment page. They enter their card details and lose money directly to the attackers. This simple trick has been reported in several major urban areas.
Restaurants and bars have also been targets. Since the pandemic, many places moved their menus to QR codes. Attackers take advantage of this shift by placing their own stickers on tables or posters. A customer scans the fake code, thinking it links to the menu. Instead, it leads to a phishing page or downloads malware onto the device.
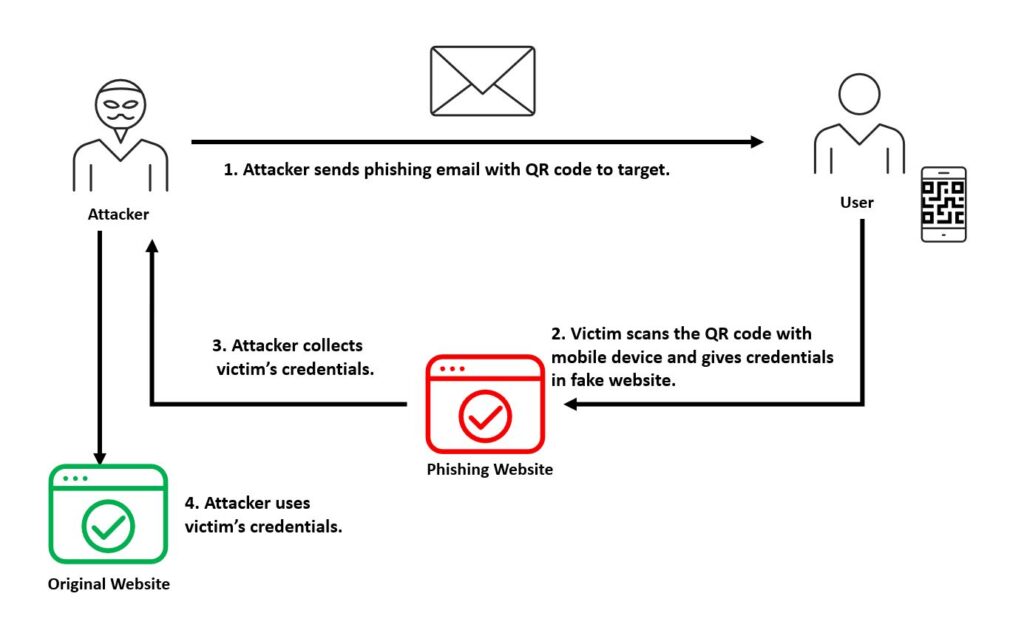
Email campaigns are another example. Security researchers have found phishing emails that replace clickable links with QR codes. The message may claim that an account is locked or a package is waiting for delivery. By scanning the QR code, the victim opens a fake login page that looks convincing. Because email filters often block known phishing links, using a QR code helps attackers bypass these defenses.
Many people face the package delivery trick. A flyer appears on your door. It says you missed a delivery. A QR code is provided to reschedule. Scanning it leads to a fake postal service site. The site asks for your address and a small redelivery fee. You lose your payment details and personal information.
A growing problem is the fake public Wi-Fi poster. These appear in airports, coffee shops, and libraries. The poster offers free internet access. You scan the code to connect. It may install a harmful profile on your phone. This gives hackers access to your data.
Some scams arrive by email. You get a message about an unlocked reward or a security alert. The email contains a QR code to “verify your account.” This bypasses link scanning in email security. It leads directly to a perfect copy of your email login page.
Another dangerous version involves downloads. You scan a code for a coupon or document. Your phone prompts you to download an app or file. This file contains malware. Once installed, it can track your activity or lock your device.
Even large companies have faced trouble. In one reported case, attackers sent QR codes to employees that looked like part of a security check. Some workers scanned the code and entered their credentials, handing attackers access to corporate systems. These types of breaches can cause not only data loss but also major damage to a company’s reputation.
These real-world examples show why quishing is not a small or rare threat. It is growing as QR codes become part of daily life. From public spaces to private inboxes, attackers are using this method because it works, and because people are not yet fully aware of the risks.
These examples show the scam’s variety. The method is always the same. A trusted context hides a malicious code. The result is always stolen information or a compromised device.
Why is Quishing So Effective and on the Rise? 👩🏼💻
Quishing is gaining ground because it takes advantage of habits people already have. QR codes are now used for payments, tickets, logins, promotions, and more. Every time someone scans a code, there is a moment of trust. Attackers know this, and they turn that trust into an easy opening. The rise in mobile payments has made the risk even bigger. In many countries, scanning a code is now the standard way to pay for food, transport, or services. That means more people are exposed every day.
Another reason quishing is spreading is lack of awareness. Most people understand the idea of a suspicious email link. They may hover over a link to check it, or ignore it if it looks strange. With a QR code, that step is not possible. The link is hidden until after you scan. Many users do not know how to check a QR code’s safety. They assume the code is safe because it is printed on an ad or sent by what looks like a trusted company.
For attackers, QR codes are cheap and simple to exploit. A printed sticker or a copied image can be created in seconds. It can then be placed over a real code in public or shared online at scale. This low cost makes quishing attractive to both small-time scammers and larger criminal groups.
The hidden nature of QR codes also makes them hard to control. Businesses may put them on posters, menus, or invoices. Once placed, it’s difficult to confirm if the code has been swapped or altered. That creates a physical risk on top of digital threats.
Email filters and security tools are another factor. Many security systems scan links in messages to block phishing. But when the link is hidden inside a QR code image, some tools fail to catch it. Attackers use this gap to sneak past defenses that would normally stop them.
The combination of wide use, low awareness, and simple execution explains why quishing is growing fast. It is not only a problem for individuals but also for companies and public services. As long as QR codes remain a common part of daily life, attackers will continue to use them as bait.
How to Detect and Prevent QR Code Phishing 🕵🏼
The best defense against quishing is awareness. While QR codes are convenient, they should never be scanned blindly. A few simple checks can reduce the chance of falling into a trap.
For everyday users, the first rule is to look at the source. If a QR code is on a random flyer, sticker, or street poster, treat it with caution. Codes placed in public spaces are easy to tamper with. Attackers often stick fake ones over real ones. Before scanning, check if the code looks out of place or poorly attached. If it seems suspicious, avoid it.
Another tip is to preview the link before opening it. Some mobile security apps and browsers show the full web address after scanning. This step lets you see if the link looks genuine. A bank’s code should not lead to a strange or shortened URL. If the address seems odd or unrelated to the service, do not continue.
Be careful with QR codes in emails as well. Attackers use them to bypass spam filters. If you receive a code claiming to fix a locked account or deliver a package, double-check with the company through their official site or app. Do not scan codes in messages from unknown senders.
For businesses, prevention starts with education. Employees should be trained to recognize quishing attempts, especially in emails. Encourage staff to verify QR codes before scanning and to report anything suspicious. Clear guidelines can stop a single careless scan from becoming a wider breach.
Companies that use QR codes for services should secure them against tampering. Placing codes in protected areas or printing them in a way that makes replacement harder can help. Some businesses now use branded or custom-designed codes that are harder to fake. Regular checks of physical codes, such as those on posters or menus, are also important.
Technical defenses also play a role. Security tools can be updated to scan QR codes for known malicious links. Multi-factor authentication is another safeguard. Even if attackers steal a password through quishing, they cannot access the account without the second step of verification.
Customers should also be guided. If a company uses QR codes, they should explain how to spot the real ones. Simple instructions, such as “only scan codes on our official website or app,” help reduce risk.
In practice, preventing quishing is about slowing down. Do not scan a code without asking where it came from and why it is there. For businesses, combine awareness, security checks, and strong authentication. Together, these steps make it harder for attackers to turn a small square of pixels into a doorway for fraud.
What to Do If You’ve Been Quished? 🤔
Acting quickly is crucial if you fall for a quishing scam. Follow these steps to limit the damage.
First, disconnect from the internet. Turn off Wi-Fi on your device. Switch to airplane mode. This stops any active data transfer. It can prevent more information from being stolen.
Do not enter any more information. Close the browser tab or app immediately. If a download started, cancel it. Do not open any files that were downloaded.
Change your passwords right away. Use a different, secure device if possible. Start with the account you just entered. Then change passwords for other important accounts. Your email and bank are top priorities.
Contact your bank and credit card companies. Tell them you may be a victim of fraud. They can watch for strange activity on your accounts. They can also block your cards and issue new ones.
Scan your device for malware. Use a reputable security app to check your phone or computer. Remove any suspicious files or programs it finds. This is especially important if you downloaded anything.
Report the incident to the proper groups. Tell your company’s IT team if it happened at work. They can protect the wider network. For personal scams, report it to the FTC at ReportFraud.ftc.gov.
Check your accounts for strange activity. Look for unknown logins or new charges. Set up account alerts if you can. These warnings tell you about login attempts or money transfers.
Consider a credit freeze. This stops anyone from opening new accounts in your name. It is a strong step if you entered your Social Security number. You can temporarily lift the freeze when you need to apply for credit.
Tell other people about the scam. If the code was in a public place, warn others. If it was a work email, let your coworkers know. This can prevent more people from becoming victims.
Learn from the experience. Think about what tricked you. Use that knowledge to be more careful next time. Everyone makes mistakes. The important thing is to improve your security habits.
These steps help you regain control. They minimize harm and protect your information. Quick action makes a big difference.
Future of QR Code Security 🔐
The future of QR code security will depend on both technology and awareness. As quishing becomes more common, new tools and standards are being developed to reduce the risk. At the same time, businesses and users will need to change how they handle QR codes.
One area of progress is smarter scanning tools. Security apps and mobile operating systems are starting to add features that check QR code links in real time. These tools can scan a code and flag suspicious or unsafe sites before the user opens them. As artificial intelligence improves, scanners will be able to detect patterns that suggest a code is fake or linked to known attack networks. This automated defense will make it harder for criminals to spread malicious codes undetected.
Another development is the rise of secure QR code standards. Some companies are exploring encrypted QR codes that hide sensitive data and can only be read by approved apps. Others are creating branded codes with unique designs or logos that are difficult for attackers to copy. These approaches make it easier for users to trust a code’s source. Over time, official standards for secure codes may become part of everyday use, much like secure web addresses with HTTPS.
Regulation will also play a role. Governments and industry groups are beginning to recognize the risks of quishing. Rules may require companies to protect the QR codes they use, especially in sectors like banking, healthcare, and transport. These policies could push businesses to adopt stronger practices, such as regular code audits or mandatory verification steps before transactions.
Education will remain a key factor. Even the best technology cannot stop every attack if people are not alert. Future awareness campaigns are likely to focus on teaching users how to verify QR codes and avoid risky scans. Just as email safety training became standard in the workplace, QR code safety may soon be part of basic security guidelines.
Looking further ahead, QR codes may shift toward new forms of digital identity. They are already used for mobile payments, event tickets, and login systems. As this grows, attackers will continue to target them. This means security must evolve alongside adoption. Multi-factor authentication, AI-driven threat detection, and secure code design will all work together to reduce risks.
In short, the future of QR code security will be shaped by both innovation and responsibility. Smarter tools will scan and block threats. Businesses will design codes that are harder to fake. Regulators will set rules, and users will learn better habits. If these efforts align, quishing will become harder to pull off and less profitable for attackers.
Conclusion 💡
QR codes make life simple. They save time, cut out extra steps, and fit into daily routines. But this same ease has opened the door for quishing. Attackers know that most people scan first and think later. A fake code on a wall, an email, or even a bill can lead to stolen money, hacked accounts, or infected devices.
The risk is not only personal. Businesses face bigger problems when quishing hits their staff or customers. A single compromised scan can expose sensitive data, disrupt services, or damage trust built over years. In many cases, the harm lasts longer than the attack itself.
The good news is that quishing can be stopped. For individuals, the key is to slow down. Look at where the code comes from, and check the link before acting. Avoid scanning codes from random posters or emails you don’t expect. Use apps or phones that can preview and check links.
For businesses, the focus should be on both security and trust. Protect physical codes from tampering, use custom designs that are hard to fake, and update tools to scan QR links for threats. Most important, teach employees and customers what safe use looks like. A small investment in awareness goes a long way.
Looking ahead, stronger tools and standards will add another layer of safety. AI-powered scanners, encrypted codes, and new rules will make it harder for attackers to profit. But technology alone is not enough. Habits and awareness must change too.
Quishing works because it hides danger in plain sight. By understanding how it works and taking simple steps, you can keep QR codes useful without falling into traps. Share this knowledge with friends, coworkers, or customers. The more people know, the harder it becomes for attackers to succeed.
QR codes will continue to grow in use. Whether for payments, tickets, or sign-ins, they are here to stay. Staying alert, using secure tools, and spreading awareness are the best ways to make sure that convenience does not turn into a costly risk.
FAQ 🎯
What is QR code phishing (quishing)?
Quishing is a phishing attack that hides a malicious link inside a QR code. When scanned, it can steal login details, payment info, or install malware.
Can I get hacked just by scanning a QR code?
Just scanning a code will not usually hack your phone. The real danger comes after the scan. If the code leads to a fake site and you enter your login details, the attacker steals them. Some codes may also prompt you to download a malicious file, which can infect your device.
How can I check if a QR code is safe before scanning it?
You cannot see the hidden link just by looking. The best practice is to inspect the source. Is it an official, high-quality print? Or is it a cheap sticker placed over another code? If you have any doubt, do not scan it.
My phone’s camera automatically opens the link. Is that safe?
The convenience is a security risk. Your camera does not check if the link is safe; it just opens it. For better safety, consider using a dedicated QR scanner app from a trusted developer. Some of these apps show you the web address and ask if you want to proceed.
What is the difference between phishing and quishing?
Phishing and quishing have the same goal: to steal your information. Phishing usually sends a malicious link in an email or text. Quishing uses a QR code to hide that link. This helps the scam bypass email security filters that normally block bad links.
I entered my password on a fake site from a QR code. What should I do?
Change your password for that account immediately. Use a different, trusted device. If you use that password for other sites, change those too. Turn on multi-factor authentication (MFA) everywhere you can. This adds a critical extra layer of security.
Are businesses really a target for quishing attacks?
Yes, businesses are prime targets. An employee scanning a malicious code can give attackers a way into the company network. This is why employee training and multi-factor authentication are essential for any modern business’s security plan.
References 🔗
- https://www.cisa.gov/news-events/news/avoiding-social-engineering-and-phishing-attacks
- https://consumer.ftc.gov/articles/how-recognize-avoid-phishing-scams
- https://arxiv.org/html/2407.16230v1
- https://keepnetlabs.com/blog/10-real-life-quishing-attack-examples-to-strengthen-your-cybersecurity
- https://www.checkpoint.com/cyber-hub/threat-prevention/what-is-phishing/what-is-quishing-qr-phishing/
- https://www.infosecurity-magazine.com/news/hackers-qr-codes-new-quishing/
- https://security.duke.edu/security-guides/qr-code-security-guide/


